Solutions / Cybersecurity
Business Email Compromise Remediation
Business Email Compromise Requires More Than Awareness
Sophisticated, targeted, and quietly destructive, BEC attacks often evade detection by traditional tools. ATS helps organizations remediate incidents, strengthen defenses, and close the gaps that attackers exploit.

What is Business Email Compromise?
Business Email Compromise (BEC) is a targeted cyberattack where threat actors use deception—not code—to manipulate employees into transferring money, divulging sensitive information, or granting access to internal systems. It’s not a broad phishing attempt. It’s calculated. Personalized. Often invisible until the damage is done.
At its core, BEC exploits trust. Attackers may pose as a company executive requesting a wire transfer, a vendor asking for updated banking details, or a colleague sharing a seemingly urgent document. These messages are often well-written, timed to coincide with business cycles, and crafted to circumvent technical defenses.
Unlike attacks that rely on malware or brute force, BEC usually succeeds without a single compromised file. That’s why it’s become one of the most effective—and financially devastating—forms of cybercrime.
Common tactics include:
- Executive impersonation: Faking the identity of a CEO or CFO to approve high-value transactions.
- Vendor fraud: Infiltrating or spoofing a trusted supplier to reroute payments.
- Payroll redirection: Convincing HR to update an employee’s direct deposit details, fraudulent invoices or documents that spoof senior executives asking them to input credentials for access.
- HR: Receiving resumes or third-party recruiters sending documents that could be embedded with malware.
Every organization is vulnerable, especially those handling financial transactions, client data, or sensitive communications. If your employees can be persuaded by email, your business is a target.
How Business Email Compromise Attacks Work
Business Email Compromise doesn’t start with malware—it begins with observation.
Attackers often begin by researching your organization’s structure, vendors, and communication patterns. Once they have sufficient context, they employ tactics such as email spoofing, credential phishing, or compromising legitimate email accounts to initiate fraud.
A typical BEC attack unfolds in four stages:
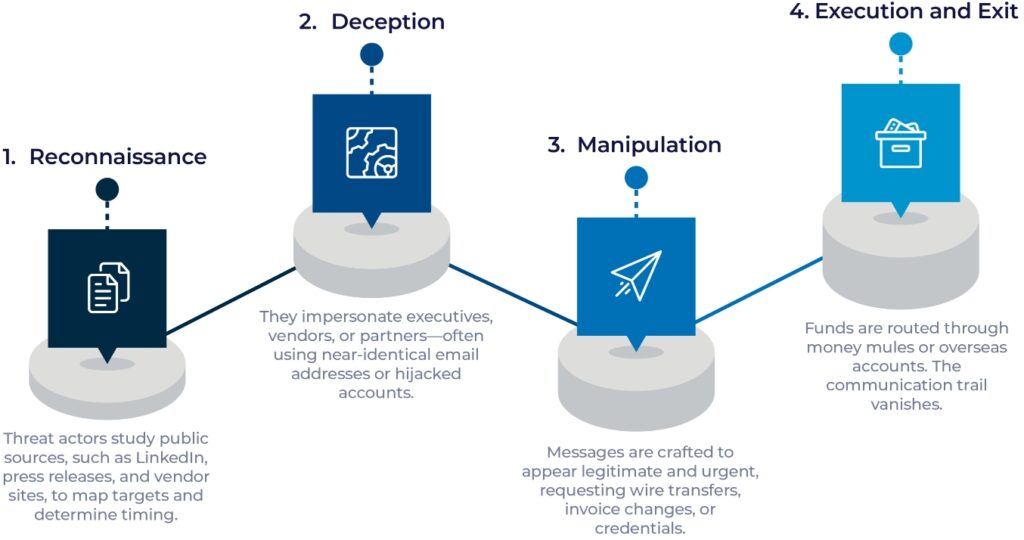
These aren’t random shots—they’re quiet, precise, and often undetected until after financial loss has occurred.
Why It’s a Growing Threat
Business Email Compromise is not a new threat, but it has evolved into one of the most financially and operationally damaging risks facing organizations today. Unlike phishing blasts or brute-force intrusions, BEC attacks are precise, patient, and often indistinguishable from legitimate communication.
The Cost Is Rising—and Underreported
According to the FBI’s Internet Crime Complaint Center (IC3), Business Email Compromise (BEC) scams have resulted in reported losses of over $55 billion globally in the last decade, with the annual U.S. loss alone exceeding $2.7 billion. And those are just the incidents that were discovered and reported. Many BEC attacks go unnoticed or are handled quietly, skewing the true scale of impact.These attacks don’t just cost money—they stall operations, strain vendor relationships, and expose internal gaps in process and oversight.
BEC Attacks Keep Getting Smarter
The newest wave of BEC campaigns utilizes real business context—derived from press releases, social media, and breached data—to craft messages that appear and feel authentic. AI-written emails now replicate voice and tone more convincingly than ever, reducing telltale signs like awkward grammar or formatting. Some attackers even time their emails to coincide with vacations, quarter-end reports, or vendor payment cycles, making them harder to flag internally.
Traditional Security Doesn’t Catch It
BEC doesn’t rely on malicious links or payloads. There’s no malware to quarantine. No firewall alert. These emails often originate from legitimate-looking domains—or in some cases, real internal accounts that have already been compromised.
That’s what makes them so dangerous: they’re invisible to tools that weren’t built to question human intent. Once trust is broken—whether between an executive and staff or between a company and its vendor—the effects ripple across departments and partnerships.
Remote Work, Supply Chains, and Faster Finance
Modern business conditions make BEC attacks easier to execute and harder to catch:
- Remote teams rely more on email than on in-person validation.
- Finance systems have automated approvals and faster transfers with fewer checks.
- Vendors operate across different time zones, making a delayed response to a fraud request seem normal.
- Turnover and onboarding gaps can leave new staff unaware of what “normal” communication looks like.
These gaps are not technical—they’re operational. And they give attackers the window they need.
With the right remediation strategy, BEC risk becomes measurable, manageable, and recoverable. ATS offers a dual focus: immediate support during a breach and long-term safeguards to prevent the next one from occurring.
How ATS Helps Prevent Business Email Compromise
Business Email Compromise thrives on human error, timing, and lack of visibility. ATS addresses each of those weak points with a structured, proactive approach customized to your organization.
Prevention strategies include:
ATS doesn’t just provide tools—we build context-aware defenses around your finance team, vendor ecosystem, and executive suite.
vCISO-led BEC Risk Assessments
Executive-level guidance to identify exposure, evaluate risk scenarios, and strengthen internal communication protocols.
Email Security Hardening
Configuration and enforcement of SPF, DKIM, and DMARC to prevent spoofing and impersonation attempts—across all business domains.
Simulated BEC and Phishing Tests
Safe, controlled campaigns designed to identify who clicks and why—followed by targeted awareness training.
Vendor and Executive Communication Protocol Reviews
Real-world gap analysis that maps your internal workflows and vendor interactions to uncover high-risk assumptions and habits.
Incident Readiness Planning
Custom playbooks, chain-of-command workflows, and internal alert triggers to keep people aligned if a BEC event unfolds.
Detection and Rapid Response
When Business Email Compromise strikes, every hour counts. These incidents often unfold quietly—no alerts, no malware, just a misdirected wire transfer or suspicious request that slips through unnoticed. ATS brings precision and calm to the chaos with a response protocol built on real-world experience.
ATS’ Experience with BEC Protection
ATS has responded to Business Email Compromise (BEC) incidents across multiple industries, including education, finance, real estate, healthcare, and hospitality. Our DFIR team brings decades of experience—both within ATS and prior to joining the firm—handling complex, high-impact threats that begin with a single email and escalate into full-scale crises. What sets us apart is not just technical depth but our ability to work under pressure, communicate clearly with stakeholders, and support clients through insurance, restoration, and recovery.
Business Email Compromise vs. Other Attacks
Business Email Compromise is often misunderstood as just another phishing scam—but the tactics, targets, and outcomes are fundamentally different. BEC doesn’t rely on malware or mass emails. It’s quiet, customized, and built to manipulate trusted relationships inside your organization.
Here’s how it compares:
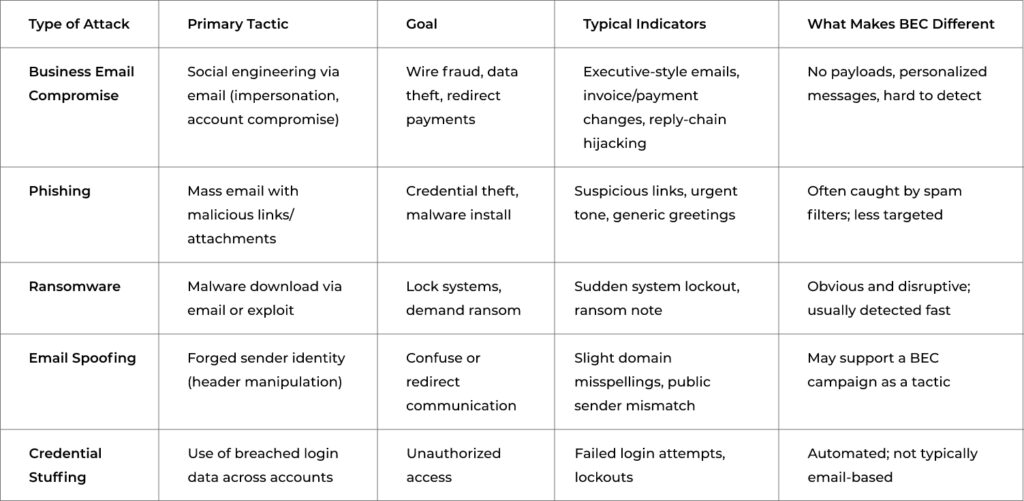
Why This Distinction Matters:
- BEC is more challenging to catch: No malware means fewer alerts.
- It bypasses technical controls: It relies on human trust, not system vulnerabilities.
- The impact is financial and immediate: BEC attacks are designed to result in direct, high-value loss.
Understanding what you’re up against helps prioritize the right controls—ones that protect people, processes, and communication flows.
Business Email Compromise isn’t a distant threat—it’s already in inboxes, waiting for a gap in process, awareness, or timing. Whether it’s a fraudulent invoice, an urgent wire request, or a subtle forwarding rule buried in an executive’s mailbox, these attacks are designed to slip past standard defenses. That’s why remediation can’t be reactive alone. It must include a forward-looking strategy, process accountability, and technical reinforcement—integrated into how your organization communicates and operates.
Protect What BEC Attacks Are Targeting
ATS brings the right combination of security leadership, hands-on response, and implementation expertise to stop BEC threats at every stage—from attempted intrusion to recovery. If you’re dealing with a BEC incident now or want to prevent the next one, we’re ready to help.
Featured Articles
Articles / Last night, the American Technology Services New York team bundled up and crunched across the ice to the...
Articles / On June 5, ATS opened its doors for NY Tech Week and turned a 6th-floor downtown office into...
Articles / Businesses and individuals face a rapidly growing menace. Account Takeover (ATO) fraud is a sophisticated cybercrime reaching alarming...
Articles / Businesses are increasingly threatened by Distributed Denial of Service (DDoS) attacks. These attacks are designed to disrupt network...



