Solutions / Cybersecurity
Ransomware Remediation
Stop the Attack. Recover Fast. Get Back to Business.
When ransomware hits, ATS moves fast. We isolate the threat, recover your data, and bring your systems back online—24/7.

Ransomware Disrupts Everything. We Get You Moving Again.
Ransomware halts operations, locks down data, and throws your business into chaos. Every second offline costs money, erodes trust, and opens the door to legal risk. Employees are stuck. Customers go elsewhere. The pressure is real—and hesitation isn’t an option.
ATS responds immediately, guiding your team through containment, recovery, and post-incident hardening. You’ll know what’s happening at every step, and you won’t face it alone.
Why Speed Matters
Data Gets Locked Fast
Encryption spreads quickly. Delay makes recovery harder.
Downtime Gets Expensive
Lost revenue. Lost productivity. Lost trust. Mid-market businesses can lose tens of thousands per hour.
Compliance Risk Rises
Uncontained ransomware can trigger fines, reporting violations, and legal exposure.
What Ransomware Attacks Can Look Like—and How We Handle Them
Ransomware doesn’t always show up the same way. Here are common scenarios businesses face—and how ATS responds:
Encryption After a Phishing Email
A single click leads to a full-system lockdown. ATS isolates endpoints, identifies the entry point, and restores operations from clean backups or recovery tools.
Backups Compromised Alongside Production Data
Some strains target backups first, eliminating easy recovery. ATS uses advanced methods, guides negotiations when necessary, and rebuilds a secure environment.
After-Hours Attack
Threat actors often strike at night or on weekends. ATS responds immediately, assessing and containing the breach—even if it wasn’t detected until morning.
Double Extortion Threats
Some attackers steal your data in addition to encrypting it. ATS helps evaluate exposure, manage legal obligations, and develop a response plan to protect your organization.
Attack Detected Mid-Execution by EDR or SOC
Sometimes encryption hasn’t started—but the attacker is already inside. ATS acts immediately to eject the threat and harden your systems before damage spreads.
Who We Help
Ransomware doesn’t discriminate—but it hits hardest when your team doesn’t have immediate, specialized support. ATS steps in for:
Small and mid-sized businesses with limited in-house security
Internal IT teams needing help during a crisis
Organizations with cyber insurance requiring expert-aligned response
Any team facing a ransomware attack, unsure what to do next
If you’re experiencing—or even suspecting—a ransomware event, you’re exactly who we help. You’re not too small. You’re not too late. You’re in the right place.
ATS Responds—Now and All the Way Through
General IT support isn’t enough in a crisis. ATS brings certified, battle-tested experts who’ve resolved ransomware attacks under pressure—quickly and thoroughly.
What sets us apart:
ATS doesn’t just provide tools—we build context-aware defenses around your finance team, vendor ecosystem, and executive suite.
Trusted by Cyber Insurers. Ready for Your Policy.
Whether you’re filing a claim or managing incidents across your client base, ATS delivers the response and documentation insurance carriers count on.
For Insured Businesses
ATS is built to work with your provider. We document every step of remediation, align with policy terms, and streamline claims—so you can recover faster with fewer roadblocks.
For Insurers And Brokers
ATS is already a trusted partner on active panels, and we’re expanding. We provide real-time containment, full forensic transparency, and policy-aligned reporting. We reduce your exposure and improve the insured’s experience—start to finish.
How We Bring You Back
1. Immediate Incident Assessment
We identify the strain, entry point, and scope—so we can act fast and with precision.
2. Threat Containment
We isolate affected systems and stop the spread.
3. Data Recovery And System Restoration
Using clean backups or advanced tools, we restore operations securely and systematically.
4. Security Hardening
We close vulnerabilities, apply protections, and help your team stay protected moving forward.
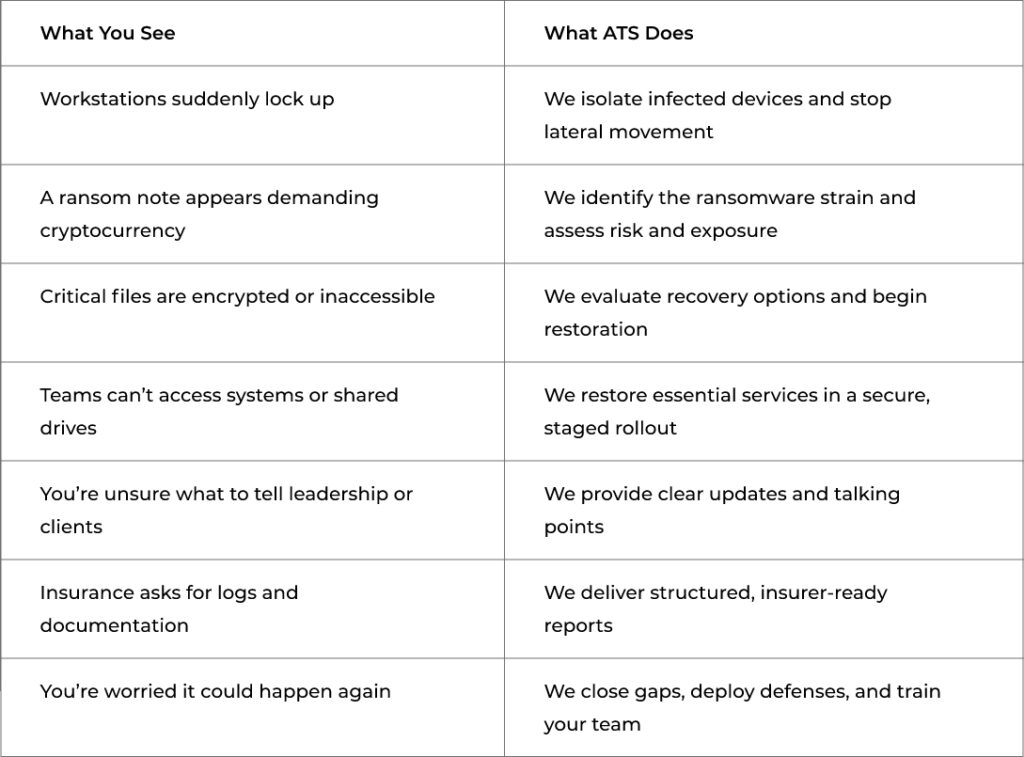
What You See vs. What We Do
Built for Cyber Insurance Support
Ransomware incidents often trigger complex insurance processes. ATS helps you navigate them without the stress.
Align With Coverage Requirements
We know what insurers expect—and we make sure your response meets the mark.
Detailed Technical Reporting
Every remediation step is logged, timestamped, and aligned with policy terms.
Faster, Cleaner Claims
No backtracking or reconstruction—we hand you a clean record for submission.
Compliance Built In
We help meet breach notification timelines and reporting obligations across regulated industries.
Ransomware Remediation FAQ
Can ATS negotiate ransom payments?
Yes. When appropriate, we manage negotiations to minimize costs and assess if payment is justified.
How fast can ATS restore my data?
We begin recovery immediately. Depending on your environment, key systems may be restored in hours to days.
Do you offer services after remediation?
Yes. We provide full cybersecurity assessments and managed services to strengthen your defenses.
Can you help with cyber insurance claims?
Absolutely. We document every step and deliver the reports you need for a smooth claim process.
What should I do after discovering ransomware?
Disconnect affected systems, avoid contacting the attacker, and call ATS immediately. We’ll take it from there.
What To Do Right Now
If ransomware has hit your network—or you think it has—take these steps immediately:
- Disconnect affected systems from Wi-Fi, VPN, and internal networks
- Do not respond to the attacker or engage with ransom demands
- Don’t delete encrypted files—they may still be recoverable
- Contact ATS for immediate support
The first few decisions make all the difference. We’ll handle the rest.
Ransomware Doesn’t Wait. Neither Should You.
Every moment offline means lost business, growing risk, and lasting damage. ATS is ready now to stop the threat, recover your data, and protect what matters most.
Featured Articles
Articles / On June 5, ATS opened its doors for NY Tech Week and turned a 6th-floor downtown office into...
Articles / Businesses and individuals face a rapidly growing menace. Account Takeover (ATO) fraud is a sophisticated cybercrime reaching alarming...
Articles / Businesses are increasingly threatened by Distributed Denial of Service (DDoS) attacks. These attacks are designed to disrupt network...
Articles / The demand (and need) for ensuring system and data security is greater than ever and increasing at an...



