Solutions / Cybersecurity
Virtual Chief Information Security Officer (vCISO)
Executive-Level Security Leadership—On Your Terms
You don’t need a full-time hire to lead like an enterprise. ATS delivers flexible vCISO services that align security strategy with your business goals—without the cost or commitment of a permanent executive.

What Is a vCISO?
A Virtual Chief Information Security Officer (vCISO) brings expert security leadership into your organization, precisely when and how you need it.
Whether you need strategic oversight, policy development, executive reporting, or compliance guidance, ATS vCISOs integrate with your team to lead with clarity and impact. Part-time, full-time, or project-based—we fit the role to your reality.
Why Organizations Choose ATS vCISO Services
Executive Strategy Without the Overhead
Get high-level security leadership without the six-figure salary and operational burden.
Scales With Your Risk and Growth
Start with 10 hours a month or embed a full-time advisor—our model flexes with you.
Compliance, Decoded
We translate frameworks like HIPAA, CMMC, NIST, GDPR, PCI, ISO 27001, and GLBA into actions your team can take.
Reports That Resonate
We speak board language—turning technical risk into clear, business-aligned insights.
What ATS vCISOs Deliver
Our vCISOs don’t just provide insight—they help execute, communicate, and lead. From strategy to operations to compliance, they bring order to complexity and action to risk.
Strategic Planning and Oversight
We help set the direction for your entire security posture.
Cybersecurity Roadmap Development
We build practical, phased plans aligned to your business goals, growth stage, and industry risks.
Executive and Board Reporting
We prepare meaningful updates and visuals that speak in business terms, not just technical jargon.
Security Leadership Representation
Your vCISO becomes a visible, respected voice in leadership conversations—internal and external.
Operational Security
Where insight meets execution.
Policy and Procedure Creation
We develop, revise, and align security documentation to standards and real-world operations.
Risk Assessment and Mitigation
We identify vulnerabilities and create prioritized action plans based on likelihood and impact.
Third-Party/ Vendor Security Management
From software vendors to service providers, we assess and monitor external risk exposure.
Compliance and Preparedness
Regulatory Readiness
We’ve guided clients through HIPAA, CMMC, NIST, GDPR, PCI, ISO 27001, GLBA, and more—with results.
Audit Support and Documentation
We organize and prepare your evidence and reports and can serve as the point of contact during audits.
Internal Training and Awareness
We deliver role-based, culture-matched training to build a stronger human firewall.
Who Benefits from a vCISO?
If any of these sound familiar, a vCISO may be precisely what your team needs:
You’re operating without a full-time CISO
But your risks, compliance pressures, or customer expectations have outgrown ad hoc solutions.
Your IT team lacks executive-level guidance
Smart technologists need leadership support to align decisions with business impact.
You’re preparing for audits, frameworks, or renewals
Compliance isn’t just about passing; it’s about being ready to defend your position.
Your board or leadership is asking hard security questions
And you need help answering with clarity and confidence.
You’ve had a security incident—or a close call
And you know it’s time to stop relying on hope as a strategy.
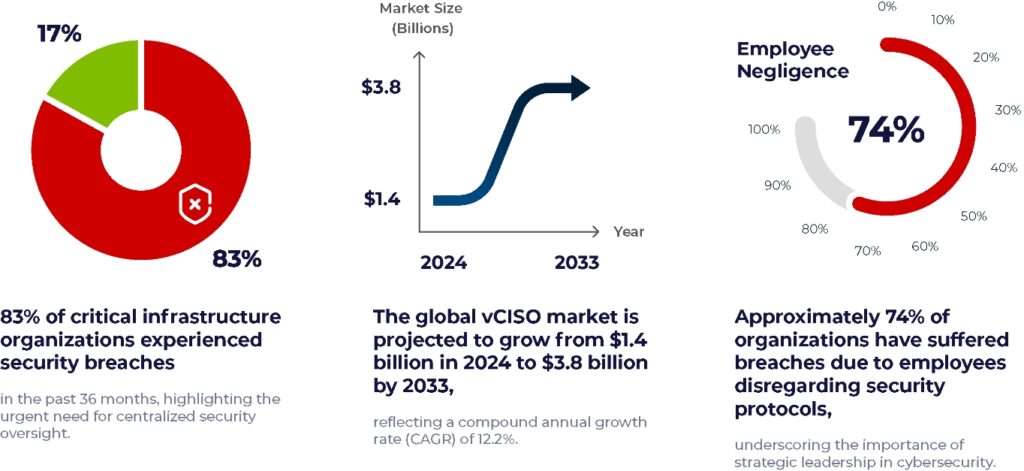
Why vCISO Services Are Gaining Momentum
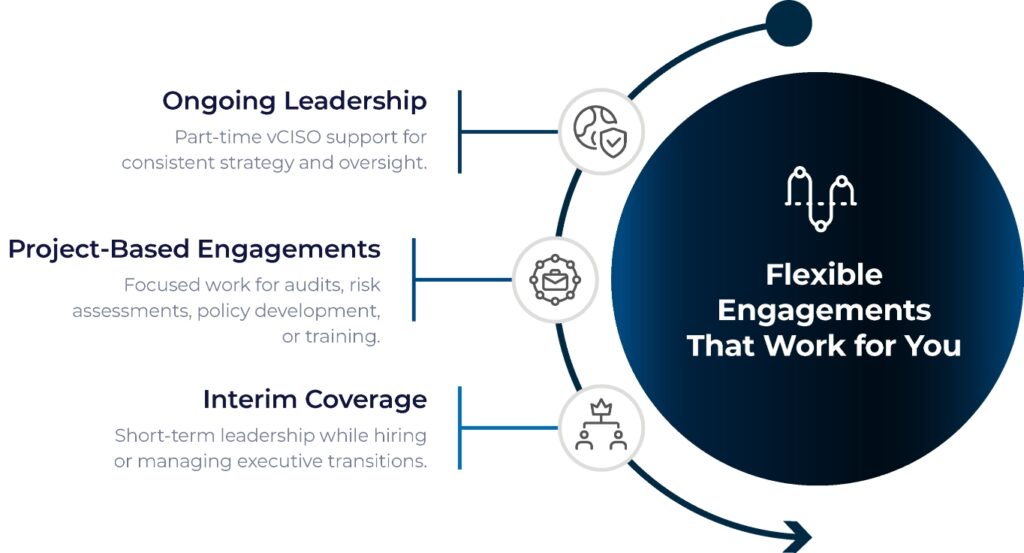
vCISO Services That Fit Your Structure
Every engagement is scoped to your systems, goals, and timeline.
vCISO FAQ
How is a vCISO different from a cybersecurity consultant?
A consultant advises. A vCISO leads. ATS vCISOs join your executive conversations, shape long-term strategy, and drive outcomes.
What qualifications do ATS vCISOs have?
Our vCISOs are senior professionals with certifications like CISSP, CISM, and CISA—plus decades of experience building programs, leading breach response, and guiding organizations through compliance and transformation.
Can a vCISO help us pass an audit?
Yes. We’ve helped clients succeed with HIPAA, CMMC, NIST, GDPR, PCI, ISO 27001, GLBA, and more. From documentation to training, we cover every step.
How fast can we start?
Most engagements begin within days of agreement. If you’re facing an audit or incident, we can mobilize faster.
Is this a short-term or long-term solution?
Either. Some clients keep their vCISO for years. Others use the service to build internal leadership and transition over time. We adapt to your timeline.
Security Isn’t Optional. Leadership Shouldn’t Be Either.
ATS vCISOs build real security programs—not paperwork. Whether you’re aiming for compliance, resilience, or confident growth, we bring the strategy and clarity to lead securely.
Featured Articles
Articles / Last night, the American Technology Services New York team bundled up and crunched across the ice to the...
Articles / On June 5, ATS opened its doors for NY Tech Week and turned a 6th-floor downtown office into...
Articles / Businesses and individuals face a rapidly growing menace. Account Takeover (ATO) fraud is a sophisticated cybercrime reaching alarming...
Articles / Businesses are increasingly threatened by Distributed Denial of Service (DDoS) attacks. These attacks are designed to disrupt network...



