Security Advisories /
Tax Season Phishing Scheme Targeting Payroll and Human Resources Professionals
Criminals are targeting payroll and HR professionals in the United States with phishing emails to gain access to employee tax records.
Summary
Criminals are targeting payroll and HR professionals in the United States with phishing emails to gain access to employee tax records. Frequently, these targeted emails impersonate an executive within an organization. They may urgently request PDF copies of employee W-2 forms, or other financial records. If given access to this information, criminals will attempt to steal refund checks, or engage in identity theft.
Details
These phishing campaigns are targeted specifically to payroll and HR staff within an organization. The attackers use public information pulled from websites and social networks to understand the roles and relationships between staff within a targeted organization. With this information, an attacker can plausibly impersonate a victim. An example email can be seen below. The red text has been changed to be used as an example.
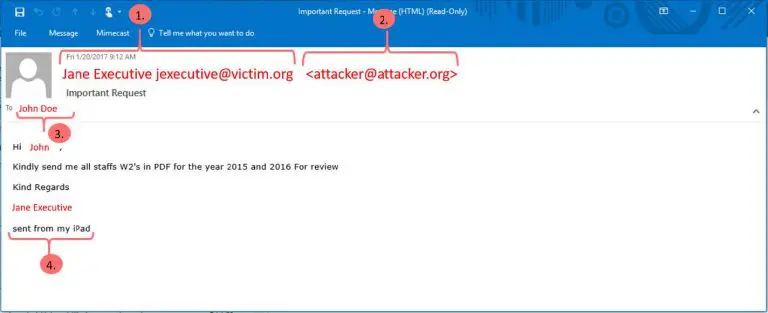
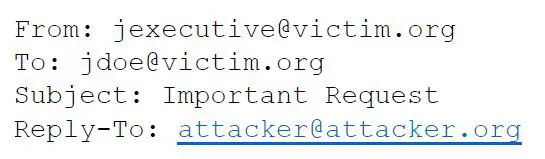 With this technique, the email appears to come from a legitimate email address within the organization. However, when the targeted user hits “reply” on their email client, the email is addressed to the attacker email address.
If a victim organization has controls in place to prevent email spoofing, the attacker may simply append the impersonated user’s email address in the “name” portion of the “From:” field to make the email more plausible, as seen in the screenshot above.
With this technique, the email appears to come from a legitimate email address within the organization. However, when the targeted user hits “reply” on their email client, the email is addressed to the attacker email address.
If a victim organization has controls in place to prevent email spoofing, the attacker may simply append the impersonated user’s email address in the “name” portion of the “From:” field to make the email more plausible, as seen in the screenshot above.
 Attackers may also use other techniques for impersonation. If a user feels that a communication is suspicious, they should be cautious.
Attackers may also use other techniques for impersonation. If a user feels that a communication is suspicious, they should be cautious.

-
- 1) The name and email of an executive was pulled from a publicly accessible source (corporate website, LinkedIn, etc.) to seem legitimate.
-
- 2) The reply address, if not internal to your organization, appears in angle brackets. This is the first hint that this email is not a legitimate request.
-
- 3) The email address of a specific employee is pulled from a publicly accessible source, as above. The attacker either knows this person works in HR/payroll or is sending the email at random in hopes that users will not report the email if it is not relevant to the user.
- 4) The ‘sent from my iPad’ signature is a clever way to mask the fact that the attacker does not know what the company’s email footer looks like. This is another red flag.
 With this technique, the email appears to come from a legitimate email address within the organization. However, when the targeted user hits “reply” on their email client, the email is addressed to the attacker email address.
If a victim organization has controls in place to prevent email spoofing, the attacker may simply append the impersonated user’s email address in the “name” portion of the “From:” field to make the email more plausible, as seen in the screenshot above.
With this technique, the email appears to come from a legitimate email address within the organization. However, when the targeted user hits “reply” on their email client, the email is addressed to the attacker email address.
If a victim organization has controls in place to prevent email spoofing, the attacker may simply append the impersonated user’s email address in the “name” portion of the “From:” field to make the email more plausible, as seen in the screenshot above.
 Attackers may also use other techniques for impersonation. If a user feels that a communication is suspicious, they should be cautious.
Attackers may also use other techniques for impersonation. If a user feels that a communication is suspicious, they should be cautious.
Guidance
It is important that payroll and HR professionals are aware of this attack and spear phishing attacks in general. Organizations should have clear policies in place that precludes sensitive, private information being sent through email. If a user has misgivings about a particular email, they should reach out to the sender in person, or through a separate channel, like telephone. In the event that an attacker successfully gains access to private information, management should be notified immediately. Management should assess the situation and proceed with steps to protect any victims. This may involve notifying the IRS and enrolling victims in identity theft protection. If you suspect that an email is malicious, please forward the email to security@networkats.com so that we may investigate further.Additional Resources
IRS Alerts Payroll and HR Professionals – https://www.irs.gov/uac/newsroom/irs-alerts-payroll-and-hr-professionals-to-phishing-scheme-involving-w2s IRS Suspicious Emails and Identity Theft – https://www.irs.gov/uac/suspicious-e-mails-and-identity-theftWorking with ATS is a breath of fresh air. ATS takes our information security concerns seriously and advises us how to avoid potential pitfalls with both hardware and software. We are beyond thrilled with ATS and only wish we had selected them a year earlier.
Joseph A. Appelbaum
President & CEO, Potomac Companies, Inc.
ATS has been our trusted partner in recent upgrades we have made to our IT infrastructure and cyber security. Their account management, project management, and technical teams have all provided top-notch service, guiding us to make informed decisions, managing timelines for multiple projects, and most of all, listening to our needs and making recommendations based on our unique work environment. During the transitions, they have kept us operating smoothly and provided quick and helpful support through their Help Desk.
Amy Gavin
Nutrition.org
I just wanted to take a moment to reach out and thank you for the excellent service you and your team have provided with the hosted SIEM solution. AlienVault is great, but the real value comes from your partnership. The appliance would not do nearly as much for us without your monitoring and consulting services. You have always been on top of things and there for us whenever there is an incident. I feel confident in that our network is secure and I am able to report that our board and clients with full assurance.
Chris Hansford
EducationWeek.org
