Security Advisories /
Phishing Attacks Simulating Federated Authentication Forms
Attackers are using phishing emails with links to landing pages that impersonate federated authentication pages from common providers such as Gmail, Office 365, Yahoo and Twitter.
Summary
Attackers are using phishing emails with links to landing pages that impersonate federated authentication pages from common providers such as Gmail, Office 365, Yahoo and Twitter. Typically, an attacker may send a link to a “secure” document or message hosted at one of these providers. The link leads to a landing page with a menu of service providers and fields to enter a username and password. Submitting any forms on this page simply gives the victim’s credentials to the attackers. The attackers may use these credentials to send spam or steal data. They may attempt to re-use the login and password combination on other services to broaden their attack.
Details
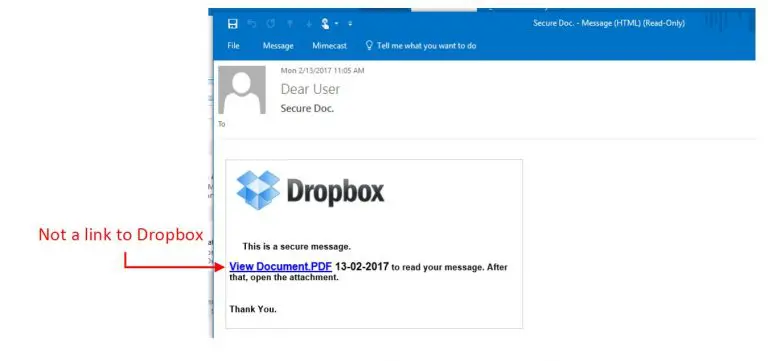 When a victim clicks on the attacker’s link, they are directed to a landing page with various login options. The login options are designed to mimic federated logins offered by these various providers. However, the forms on the page submit directly to the attacker.
When a victim clicks on the attacker’s link, they are directed to a landing page with various login options. The login options are designed to mimic federated logins offered by these various providers. However, the forms on the page submit directly to the attacker.
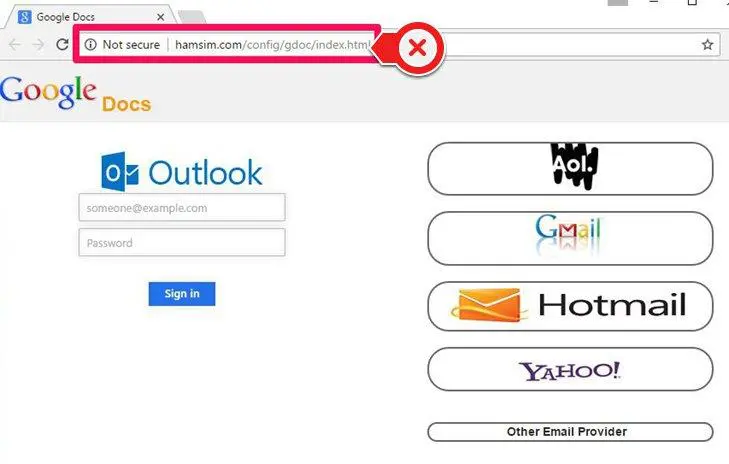 Attackers may immediately use the account to send spam email, steal information from the compromised account, or by using identical credentials on other service providers.
Attackers may immediately use the account to send spam email, steal information from the compromised account, or by using identical credentials on other service providers.
Guidance
Federated authentication from large providers such as Microsoft, Google, Twitter and Facebook are implemented for secondary services to simplify the authentication process for end-users and to speed up development. However, federated logins never give actual credentials to these secondary services. Credentials are always submitted to the federated authentication provider, with granted permissions stated clearly. An example, legitimate federated login form can be seen below.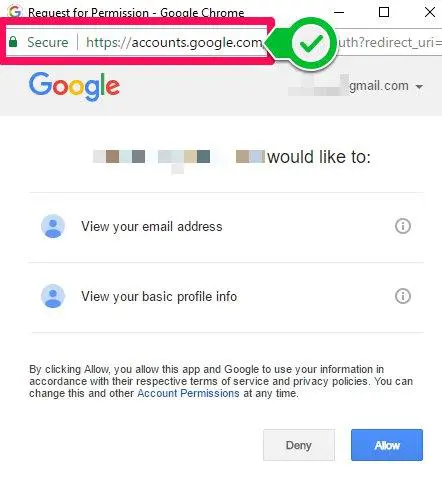 The most common method of avoiding these types of attacks is to implement Multifactor Authentication for access to any tool where corporate data is stored. This will ensure that an attacker cannot access sensitive information even if they obtain a username and password combination. Checking the address bar for the “Secure” indicator (pictured above) before typing any password is also helpful, though it is possible for an attacker to spoof that in some cases.
If you have any concerns regarding security, please reach out to your ATS Account Manager. If you have an email that you suspect to be fraudulent, please forward it to security@networkats.com for investigation.
The most common method of avoiding these types of attacks is to implement Multifactor Authentication for access to any tool where corporate data is stored. This will ensure that an attacker cannot access sensitive information even if they obtain a username and password combination. Checking the address bar for the “Secure” indicator (pictured above) before typing any password is also helpful, though it is possible for an attacker to spoof that in some cases.
If you have any concerns regarding security, please reach out to your ATS Account Manager. If you have an email that you suspect to be fraudulent, please forward it to security@networkats.com for investigation. Working with ATS is a breath of fresh air. ATS takes our information security concerns seriously and advises us how to avoid potential pitfalls with both hardware and software. We are beyond thrilled with ATS and only wish we had selected them a year earlier.
Joseph A. Appelbaum
President & CEO, Potomac Companies, Inc.
ATS has been our trusted partner in recent upgrades we have made to our IT infrastructure and cyber security. Their account management, project management, and technical teams have all provided top-notch service, guiding us to make informed decisions, managing timelines for multiple projects, and most of all, listening to our needs and making recommendations based on our unique work environment. During the transitions, they have kept us operating smoothly and provided quick and helpful support through their Help Desk.
Amy Gavin
Nutrition.org
I just wanted to take a moment to reach out and thank you for the excellent service you and your team have provided with the hosted SIEM solution. AlienVault is great, but the real value comes from your partnership. The appliance would not do nearly as much for us without your monitoring and consulting services. You have always been on top of things and there for us whenever there is an incident. I feel confident in that our network is secure and I am able to report that our board and clients with full assurance.
Chris Hansford
EducationWeek.org
