Security Advisories /
Google Docs Phishing Attack
With permission, the attacker has the ability to read and send from the users email account as well as manage contacts.
Summary
Yesterday afternoon a unique phishing attack impersonating Google Docs quickly began spreading via email. The email appeared to be sharing a Google Doc and contained a link to a legitimate Google webpage, requesting permissions to your account. If you granted the permissions, the attacker had the ability to read and send from your email account as well as manage your contacts.
Details
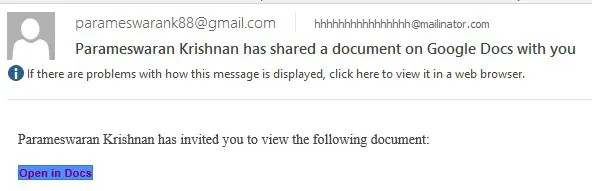
The scam starts with an email from someone that has sent you an email before, who had likely been recently compromised. This email looks legitimate but you can see it includes an unexpected ‘To:’ address as shown below. This is an indicator of an illegitimate email.
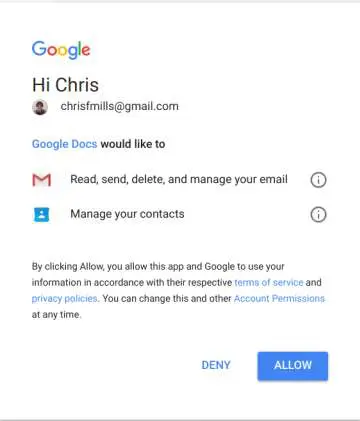
 The link leads to a legitimate Google page requesting full permissions for an extension called ‘Google Docs’ to your email and contacts. This extension is malicious and is not the real Google Docs. Granting these permissions will result in your account immediately sending the same email to everyone you have ever emailed. Additionally, the attacker has permissions to your account which can be used for further attacks.
The link leads to a legitimate Google page requesting full permissions for an extension called ‘Google Docs’ to your email and contacts. This extension is malicious and is not the real Google Docs. Granting these permissions will result in your account immediately sending the same email to everyone you have ever emailed. Additionally, the attacker has permissions to your account which can be used for further attacks.
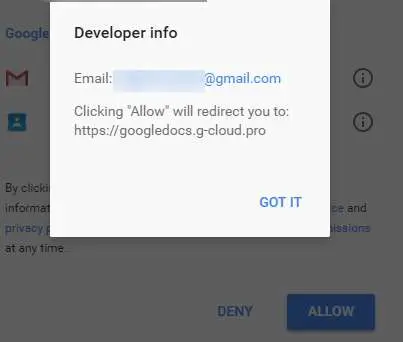
 Clicking on the ‘Google Docs’ link on this permissions page reveals that the web app was developed by a miscellaneous Gmail account. Clicking ‘Allow’ will grant that Gmail user access to your account.
Clicking on the ‘Google Docs’ link on this permissions page reveals that the web app was developed by a miscellaneous Gmail account. Clicking ‘Allow’ will grant that Gmail user access to your account.
 What makes this attack significant is the malicious use of a real web app developed for Google accounts. You were not directed to a page impersonating Google, as is typical for these types of attacks. Instead, you were being asked by Google to give permissions to an attacker.
While Google quickly reacted to shut down this scam and disable the affected accounts, this method is likely to be seen again. Attackers now have a blueprint for more effective phishing attacks in the future.
What makes this attack significant is the malicious use of a real web app developed for Google accounts. You were not directed to a page impersonating Google, as is typical for these types of attacks. Instead, you were being asked by Google to give permissions to an attacker.
While Google quickly reacted to shut down this scam and disable the affected accounts, this method is likely to be seen again. Attackers now have a blueprint for more effective phishing attacks in the future.
 The link leads to a legitimate Google page requesting full permissions for an extension called ‘Google Docs’ to your email and contacts. This extension is malicious and is not the real Google Docs. Granting these permissions will result in your account immediately sending the same email to everyone you have ever emailed. Additionally, the attacker has permissions to your account which can be used for further attacks.
The link leads to a legitimate Google page requesting full permissions for an extension called ‘Google Docs’ to your email and contacts. This extension is malicious and is not the real Google Docs. Granting these permissions will result in your account immediately sending the same email to everyone you have ever emailed. Additionally, the attacker has permissions to your account which can be used for further attacks.
 Clicking on the ‘Google Docs’ link on this permissions page reveals that the web app was developed by a miscellaneous Gmail account. Clicking ‘Allow’ will grant that Gmail user access to your account.
Clicking on the ‘Google Docs’ link on this permissions page reveals that the web app was developed by a miscellaneous Gmail account. Clicking ‘Allow’ will grant that Gmail user access to your account.
 What makes this attack significant is the malicious use of a real web app developed for Google accounts. You were not directed to a page impersonating Google, as is typical for these types of attacks. Instead, you were being asked by Google to give permissions to an attacker.
While Google quickly reacted to shut down this scam and disable the affected accounts, this method is likely to be seen again. Attackers now have a blueprint for more effective phishing attacks in the future.
What makes this attack significant is the malicious use of a real web app developed for Google accounts. You were not directed to a page impersonating Google, as is typical for these types of attacks. Instead, you were being asked by Google to give permissions to an attacker.
While Google quickly reacted to shut down this scam and disable the affected accounts, this method is likely to be seen again. Attackers now have a blueprint for more effective phishing attacks in the future.
Guidance
If you granted access to this malicious extension, Google suggests going to this site: http://g.co/SecurityCheckup and removing any apps you do not recognize. If you see one called ‘Google Docs’ remove it immediately. The real Google Docs has access to your account by default.- Keeping a ‘think before you click’ mentality with links and attachments in email. Taking a second look before clicking could save you or your organization a lot of time and money. Do not be afraid to ask for help if you are not sure if a link is safe.
- Performing the Security Checkup, linked above, on a regular basis. This is a great way to keep tabs on what has permissions to your account and where your account is being accessed.
- Implementing Multifactor Authentication on your account. This requires access to your phone as well as your password to log in to your account and can be implemented for personal and business Google accounts.
Working with ATS is a breath of fresh air. ATS takes our information security concerns seriously and advises us how to avoid potential pitfalls with both hardware and software. We are beyond thrilled with ATS and only wish we had selected them a year earlier.
Joseph A. Appelbaum
President & CEO, Potomac Companies, Inc.
ATS has been our trusted partner in recent upgrades we have made to our IT infrastructure and cyber security. Their account management, project management, and technical teams have all provided top-notch service, guiding us to make informed decisions, managing timelines for multiple projects, and most of all, listening to our needs and making recommendations based on our unique work environment. During the transitions, they have kept us operating smoothly and provided quick and helpful support through their Help Desk.
Amy Gavin
Nutrition.org
I just wanted to take a moment to reach out and thank you for the excellent service you and your team have provided with the hosted SIEM solution. AlienVault is great, but the real value comes from your partnership. The appliance would not do nearly as much for us without your monitoring and consulting services. You have always been on top of things and there for us whenever there is an incident. I feel confident in that our network is secure and I am able to report that our board and clients with full assurance.
Chris Hansford
EducationWeek.org
