Articles /
How You Can Keep Your Organization Safe from a Cyber-Attack
When thinking about security, the first thought that comes to mind for most people is password safety. While you most certainly shouldn’t write your password on a sticky note and stick it to your laptop, network security goes beyond just passwords. But to protect your entire organization, it goes beyond just any one aspect or single solution.
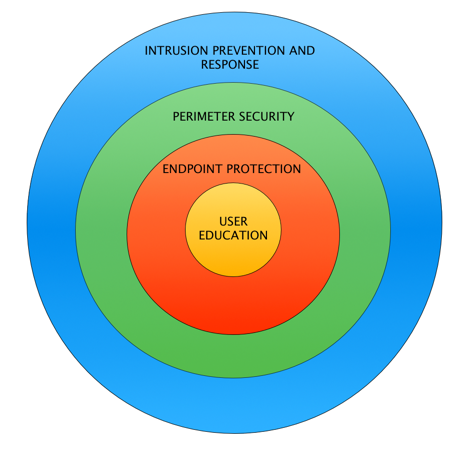
Today, organizations need to take a multi-layered, comprehensive approach to security. The chart below illustrates the core components of a holistic security effort:
As illustrated, the core and probably the most important component of IT security is User Education, as even the most sophisticated security tools can be ineffective in the face of user carelessness. According to SC Magazine, over 52% of organizational security breaches in the U.S. are caused by human error. These errors could be avoided by simply educating employees about security risks as well as implementing clear policies and procedures for employees to follow.
As you move away from the center the next ring is Endpoint protection. It usually consists of security software installed on end-user machines such as antivirus, data encryption, antimalware, etc. Many of these tools run intelligently in the background protecting systems from malicious files containing malware, phishing attacks, key loggers, backdoors, spyware and other computer threats.
Perimeter Security, the next layer, aims to safeguard an organization’s network from external threats. These systems include firewalls, messaging and content filtering, etc. Much like the fence around your house they prevent malicious content from entering your network. They are typically a combination of onsite devices and can also include third party cloud security services.
The final layer is Intrusion Prevention and Response is the most proactive and comprehensive service an organization can use that doesn’t want to invest in its own dedicated team of security experts. It leverages technology to identify and prevent any threats originating internally or externally to the network.
There are also new tools that could add another layer or integrate with other tools such as event management and threat detection, which can provide some early warning capabilities, that allow you to prepare or harden your defenses for a possible attack.
A comprehensive view of IT security is paramount to all data driven organizations. Without it, you may be subjecting your organization to unnecessary risks. Remember, the first step to any comprehensive IT security plan is education. Educate your staff on what it means to stay safe in the digital age of cyber-attacks and protect your organization today. I will be putting together some content specifically around user education in the upcoming weeks, so look forward to that!