Solutions / Cybersecurity
Continuous Threat Exposure Management (CTEM)
Reduce Vulnerabilities with Continuous Threat Exposure Management (CTEM)
Picture your company’s attack surface as a sprawling, constant-construction city—new streets carved overnight, shadowy alleys twisting unpredictably, and blind spots lurking around every corner. CTEM serves as an always-on surveillance team, continuously uncovering vulnerabilities and identifying weak points before they become entryways for disaster.
While the average organization takes 270 days to detect and contain a breach, continuous threat exposure management rewrites the narrative. Powered by a team of cybersecurity specialists, ATS’ CTEM delivers real-time risk mapping, constant monitoring, and proactive threat identification.

Continuous Threat Exposure Management (CTEM) provides a proactive, strategic framework to:
Identify vulnerabilities across the attack surface in near real-time.
Prioritize risks based on potential impact and severity.
Mitigate cyber threats with precision and confidence.
CTEM reduces cyber risks, outpaces threats, and aligns security spending with business goals.
Why CTEM Matters: Addressing Modern Cyber Risks
The digital terrain is shifting, fast. With the surge in cloud adoption, remote workforces, and expanding integrations of third-party vendors and SaaS solutions, organizations face a labyrinth of complexity within their systems, networks, and databases. These shifts create environments where risks can emerge unexpectedly, exposing organizations to threats that traditional methods fail to detect.
Leveraging a data-driven, forward-thinking approach, ATS’ CTEM team uncovers, assesses, and neutralizes vulnerabilities before they ignite into full-blown attacks. It’s more than a service; it’s a strategy for navigating the unpredictable.
Maximizing Security Impact with CTEM
A well-executed Continuous Threat Exposure Management (CTEM) program delivers far-reaching benefits: fortifying your security posture, sharpening decision-making, and ensuring every resource drives measurable impact.
Proactive Risk Management
With ATS’ CTEM, vulnerabilities are dealt with before becoming a threat. Real-time threat intelligence and 24/7 monitoring enable organizations to proactively foresee risks and close security gaps. This forward-thinking approach reduces exposure to cyberattacks and instills confidence in your overall security strategy.
Strengthen Operational Resilience
CTEM doesn’t stop at identifying risks—it actively reinforces your defenses to ensure uninterrupted business operations. By analyzing your attack surface through an adversary’s lens, ATS identifies critical vulnerabilities and locks them down.
When incidents occur, CTEM equips your organization with rapid insights and targeted remediation, minimizing the fallout. It’s a system built for resilience, reducing the likelihood of breaches and ensuring business continuity by avoiding costly downtime and disruption.
Smarter, Data-Driven Decisions
Effective cybersecurity thrives on clarity and precision. CTEM empowers executives and security leaders with actionable insights, bridging the gap between technical risks and strategic business objectives. By zeroing in on vulnerabilities that pose the greatest threat to mission-critical assets, you can recalibrate your focus—channeling resources where they deliver maximum impact.
This isn’t just data; it’s a narrative that speaks to the boardroom and the security operations center alike. Make smarter, sharper decisions. Optimize every investment. And evolve your security strategy with the confidence that comes from understanding what matters most.
Cutting Costs with Smart Security
Cyber incidents don’t merely bruise the bottom line—they rip it apart. Ransomware payouts. Regulatory fines. Tarnished reputations. Paralyzed operations. These aren’t hypotheticals; they’re inevitable without a strategy that stays ahead of threats.
Continuous Threat Exposure Management allows ATS to tackle vulnerabilities at their root, closing gaps and streamlining defenses long before threats take shape. It’s precision engineering for your security posture—eliminating redundancies, optimizing workflows, and cutting the bloated costs of cybersecurity ownership. The result? A leaner, more effective approach that protects not your assets and your reputation.
A strong reputation doesn’t just shield against damage—it builds bridges of trust. It earns loyalty from stakeholders, inspires confidence in customers, and fuels sustainable growth. With CTEM, security becomes more than a defense—it’s a cornerstone of resilience, credibility, and enduring success.
Regulatory Compliance
The regulatory landscape is tightening its grip. With rising data privacy laws and cybersecurity benchmarks, compliance isn’t optional—it’s a gateway to credibility. Continuous Threat Exposure Management (CTEM) ensures your organization aligns seamlessly with frameworks like NIST, ISO 27001, and GDPR, protecting systems and sensitive data before vulnerabilities become violations.
Compliance isn’t just a box to check—it’s a statement of accountability. CTEM mitigates risks that could derail operations and demonstrates your commitment to transparency. The result? Confidence to face the regulatory maze head-on while cultivating trust among customers, partners, and stakeholders.
But CTEM doesn’t stop at compliance. By sharpening risk management, improving resilience, and supplying leaders with actionable insights, CTEM equips organizations to outpace emerging cyber threats. It’s a platform for growth—securing your data and your operational and financial ambitions.
ATS’ CTEM Program
ATS’ CTEM offering is designed to provide organizations with a high level of protection through continuous visibility, actionable intelligence, and expertly deployed cyber strategies. Our program leverages advanced tools and best practices to deliver tangible improvements in cybersecurity posture.
Key Features of ATS’ CTEM Services
1. Cybercrime Attack Surface Visibility
Understand your organization’s vulnerabilities and risks through the lens of an adversary. This perspective enables precise prioritization of security measures that protect your most critical assets.
2. Monitoring and Alerts
ATS’ managed monitoring solutions focus on your organization’s needs, delivering decisive action for your most pressing concerns.
3. Threat Intelligence
The threat landscape changes daily, but with ATS, you’re a step ahead. ATS helps you strengthen defenses and act decisively before vulnerabilities can be exploited.
CTEM in Action: The Five Stages of Risk Management
CTEM’s structured approach ensures that every aspect of your attack surface is addressed comprehensively and efficiently:
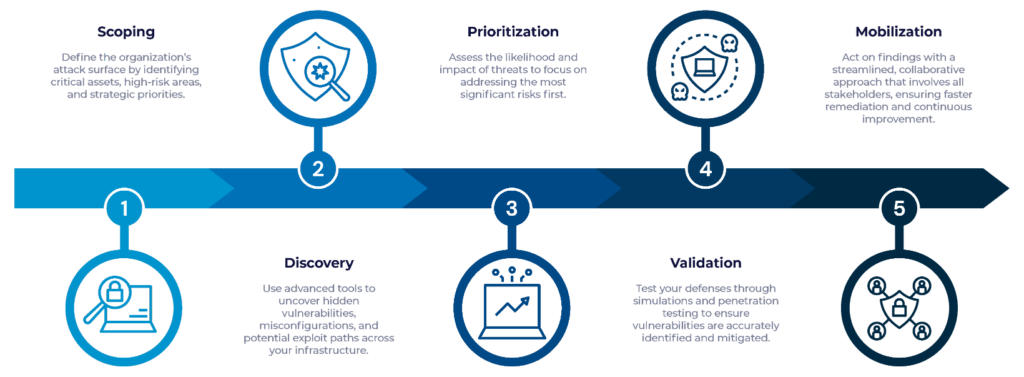
CTEM: A Strategic Advantage for Executives
For executives, Continuous Threat Exposure Management (CTEM) is more than a cybersecurity framework—it’s a catalyst for smarter, stronger business operations. For executives, it’s the bridge between understanding risk and harnessing it to drive measurable impact. CTEM enables organizations to cut through uncertainty, fortify resilience, and focus on operations. CTEM drives measurable advancements in risk reduction, operational efficiency, and organizational resilience.
Why Executives Choose CTEM:
- Gain clarity into your organization’s risk exposure and security investments.
- Demonstrate a proactive approach to stakeholders, investors, and regulators.
- Leverage real-time insights to support innovation without compromising security.
Build Your Future-Ready Security Posture Today
ATS’ Continuous Threat Exposure Management (CTEM) program equips your organization with the tools to outpace risks. Protect your assets, improve resilience, and face cybersecurity challenges confidently.
Contact Us to Start Your Project
Don’t just react to threats—anticipate and overcome them. Begin your CTEM journey with ATS.
Featured Articles
Articles / Last night, the American Technology Services New York team bundled up and crunched across the ice to the...
Articles / On June 5, ATS opened its doors for NY Tech Week and turned a 6th-floor downtown office into...
Articles / Businesses and individuals face a rapidly growing menace. Account Takeover (ATO) fraud is a sophisticated cybercrime reaching alarming...
Articles / Businesses are increasingly threatened by Distributed Denial of Service (DDoS) attacks. These attacks are designed to disrupt network...



