Articles /
The Keys to CMMC Compliance
The Department of Defense (DOD) has published a new set of cybersecurity requirements for doing business with the Department: The Cybersecurity Maturity Model Certification (CMMC). By 1 October 2025, every DOD contractor will be required to obtain a CMMC certification.
CMMC compliance is critical to DoD contractors, but the CMMC compliance process can be complex and confusing.
Register now for the 1st in our free live webinar series, Wednesday, February 3 at 1 p.m. EST.
Why is CMMC Necessary?
Unfortunately, the Defense Industrial Base (DIB), comprised of an estimated of 220,000 companies, lacks adequate cybersecurity. Intellectual property theft from the DIB costs companies an estimated $600 billion annually. Recognizing the problem and the devastating economic impacts on the government and industry, the DOD has unveiled the CMMC as the path towards hardening the DIB.
The Secretary of the Navy published a Cybersecurity Readiness Review in March 2019 which states, “The systems the U.S. relies upon to mobilize, deploy and sustain forces have been extensively targeted by potential adversaries, and compromised to such extent that their reliability is questionable.” The report continues, “Despite forward-leaning efforts by the DIB Executive Steering Committee (ESC), the DIB continues to hemorrhage critical data.”
Organizations of all sizes are attacked on a daily basis, and without a robust cybersecurity program in place, those attacks go unnoticed by the victims– even the successful ones. While cybersecurity is not a new requirement in DOD acquisition, the CMMC makes cybersecurity foundational in all contracts.
Making Security Foundational
The CMMC requires cybersecurity controls to be verified by an independent third party called CMMC Third-Party Assessor Organization (C3PAOs.) Certified assessors employed by C3PAOs will conduct assessments of DOD contractors’ unclassified networks. Upon a successful assessment of a company’s unclassified network, the C3PAO will grant that company the appropriate CMMC certification. A CMMC certification is not required to bid on a DOD contract, but a company bidding on a contract with the CMMC requirement must be granted a CMMC certification at the DOD directed Maturity Level (or a higher level) by the time of contract award.
As stated by Andy Stewart, Senior Federal Strategist, Cisco, “This [the CMMC] couldn’t come at a more critical time. The aftermath of the SolarWinds hack is a sharp reminder of the importance of securing supply chains from cybersecurity vulnerabilities.”
Publication of CMMC and the CMMC Accreditation Body
DOD released Version 1.0 of the CMMC in January 2020, and an updated version (Version 1.02) in March 2020.
In January 2020, the CMMC Accreditation Body (CMMC-AB) was formed by a volunteer group of cybersecurity and consulting professionals from across the United States. The CMMC-AB has been charged by the DOD with training and certifying the cadre of CMMC assessors that will grant CMMC certifications to the entire DIB.
Who is Impacted by CMMC? Do We Really All Need It?
Every organization doing business with the DOD will need to get certified-except those companies that solely produce Commercial-Off-The-Shelf (COTS) products and companies with contracts below the micro-purchase threshold. Every DOD contractor will need to achieve at least a CMMC Maturity Level 1, which is equivalent to the FAR 52.204-21 requirements to safeguard Federal Contract Information (FCI). Any company that processes, transmits, stores, or otherwise handles Controlled Unclassified Information (CUI) will need to achieve at least a CMMC ML 3.
The CMMC Maturity Levels
Each CMMC maturity level has associated controls and processes. The CMMC adds additional requirements to the NIST SP 800-171 controls, necessitating more elevated controls at each higher maturity level. Each of the maturity levels are cumulative, meaning that to achieve ML3 a company must also comply with ML 1 and ML 2.
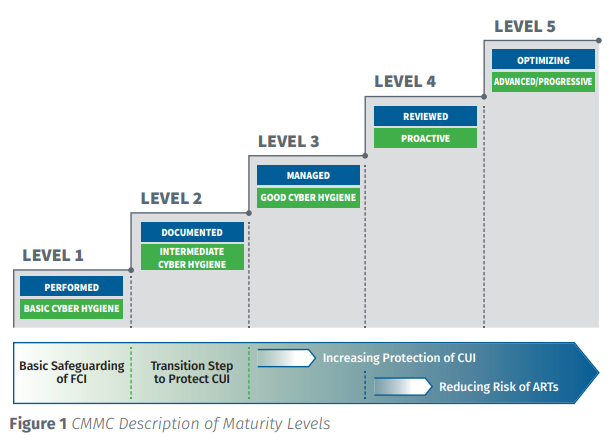
While the CMMC ML1 through ML3 are based on NIST SP 800-171 Revision 2, the CMMC domains vary slightly from the NIST domains [families].
DFARS Interim Rule
On December 1, 2020, the interim rule which amends the DFARS to implement the CMMC went into effect. In addition to introducing the DFARS clause implementing the CMMC, this rule amends DFARS subpart 204.73, Safeguarding Covered Defense Information and Cyber Incident Reporting, to implement the NIST SP 800-171 DoD Assessment Methodology.
While the DFARS interim rule directs the inclusion of the new DFARS clauses into new solicitations gradually over the next few years, the DoD and large prime contractors have already begun to require companies to conduct a NIST 800-171 self-assessment and report the score into SPRS, even if companies do not process, transmit, or store CUI.
Roadmap to Certification – Register for the Webinar
CMMC compliance is two things.
- Absolutely critical for defense contractors
- Nuanced and confusing
With a series of free webinars, ATS will provide all of the keys necessary to understand CMMC compliance starting with “NIST 800-171 Self-Assessment and the CMMC,” Wednesday, February 3 at 1 p.m. EST. In subsequent webinars, we’ll cover other topics that will help you get and maintain that critical CMMC Compliance certification.
CMMC compliance is easier when you know how to connect the dots. To get started, download our eBook now and register for the webinar on February 3rd.